We noticed that computers running Windows 10 1803 does not auto-enroll client authentication certificate (PKI) after OSD has ended. The client actually does not get any certificates before a user logs on..
This results in clients fresh out of OSD just sitting there, not getting any policies and therefore not any deployments, CI’s and so on..
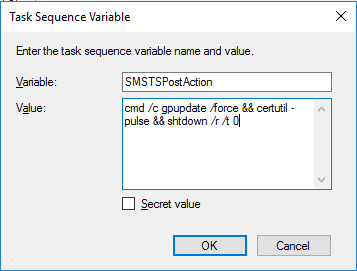
We fixed it in our TS by adding a “Run CMD command” step at the end with the command “certutil -pulse” which triggers certificate enrollment.
You’ll need to create “SMSTSPostAction” variable in the task sequence with the following commands: